This blog post provides an introduction to Quantum Security, launches QuBites season 3, outlines potential security scenarios and shares what organizations can do now to prepare for Q-Day, the day when Quantum Advantage will be readily available and deprecating today’s cryptography.
Quantum Computing (QC) is probably the most disruptive emerging technology in computing. Quantum Computing offers solutions for computational expensive problems which are currently not solvable in a reasonable time with current, classical computers – even with large supercomputers and advanced hardware. Quantum computing is without a doubt a topic we have kept an eye on for a while. Both business and tech leaders should keep an eye on it as well, as it has the potential to be the most disruptive technology in computing to date. While true Quantum Advantage is not here yet, there’s no doubt it will happen mid-term and will introduce a new threat to current standard cryptography that makes up the foundation for today’s secure communication.
If you are not familiar with Quantum Computing, it’s recommended to start with our introductory post and to watch the first episode of QuBites, our video series about approachable Quantum Computing.

The Need for Cybersecurity
Security and privacy are top of mind for many business leaders today. For most large organizations hacker attacks and the data breaches, fraud and other cybersecurity issues they can lead to are a daily concern. To makes things more challenging, these attacks are typically not singularly focused on a particular line of business. Often, they spawn across all departments of a company, including customer data.
Maintaining security ensures trust and is therefore a key piece of the business. Market research firms like Forrester predict and analyze digital security shifts1 as attacks increase both in volume of destruction and level of sophistication. Business leaders no longer ask how secure the company is but rather how ready they are to respond immediately. In a humorous twist of irony, most organizations are looking to Zero Trust models that establish trust by eliminating trust in the network architecture. This initiative focuses on not only preparing for the worst cases but actually designing their systems around it, assuming worst intent by all accessing their networks, applications, and environment.
Modern cybersecurity does not only affect an enterprise’s computer network like office PCs, but also all mobile devices, personal employee devices, and every machine potentially accessing their environment. Even small IoT devices. In fact, in a recent Forrester IoT Security Report2, global security decision-makers on average indicated that 10% of their security budget will go to IoT Security, making IoT Security a spending priority. With a further increase of 10% - 14% expected in the coming years.
Quantum Security – A Threat
Today’s digital privacy and security relies on encryption algorithms with Public-Key (asymmetric) or symmetric cryptography. For example, the famous asymmetric algorithm, RSA, is the basis of every secure web session with HTTPS or instant messaging encryption. Whereas other encryption algorithms are used for blockchain, crypto currencies, finance, signatures, and multiple other places. Asymmetric encryption is basically the basis for our secure communication today, making the rise of Quantum Computing a threat for (internet) security as we know it.
Why? Encryption algorithms are based on prime numbers which are very hard to factorize, making attacks very time consuming even on the most powerful classical computers. Quantum Computers work differently and can perform Shor’s algorithm with prime number factorization in polynomial time. Meaning a private cryptography key can be calculated in a short amount of time, making it practical to crack RSA-encrypted data.
Current calculations predict it would take a classical computer 300 trillion years to crack an RSA-2048 encryption key, whereas a Quantum Computer with 4099 stable Qubits can perform the same attack in just 10 seconds! This requires a powerful Quantum Computer with enough stable Qubits, which is not available as of today but there’s little doubt it will happen sooner or later. Once it happens basically all secure communication as we know it, is not secure anymore. Some experts call this upcoming day the Q-Day or Years-2-Quantum (Y2Q) day, in reference to the Y2K scare you may remember. Aka, the Millennium bug. Q-Day will happen when large-scale Quantum Computers can execute Shor’s algorithm to crack RSA-2048 bit, currently the largest RSA number. Quantum experts prognose a Quantum Computer that powerful could be available in 5 to 30 years. IBM announced they will have a 121-Qubit Quantum Computer by the end of 2021. And by the end of 2023, a 1000 Qubits Quantum Computer in the cloud. It should also be considered that unforeseeable, disruptive breakthroughs happen all the time in technology and with the infancy of the QC field, it’s likely that Q-Day might happen sooner or at least in the lower end of the 5-30 years’ time horizon.
Analysts say that getting started now is more imperative than ever. What can be done now to prepare for the inevitable Q-Day? Plenty of things. There’s great research for post-quantum cryptography algorithms that are resistant to Shor’s prime factorization and similar numeric attacks. These algorithms are expected to replace RSA and similar in the mid-term and should be available before Q-Day (hopefully). However, the logistics for swapping out encryption algorithms at an internet scale will be huge and takes time. One key paradigm shift to speed this up, that can already be implemented now, is so called Crypto Agility which allows a system to rapidly switch between cryptography algorithms and not be hard wired in distributed code repositories. Techniques like DevSecOps for example, allow us to quickly exchange server certificates with crypto service gateways and similar technology.
You can read more about DevSecOps and other Cybersecurity business innovations here and/or reach out to our security expert team. We can help you assess/audit your current state and provide expert guidance on the specific actions your business should take to mitigate the risk of Q-Day before it arrives.
Quantum Cryptography – An Opportunity
Where there’s shadow, there’s also light and the random nature of quantum mechanical events allows the build of commercially available True Random Number Generators. These are important since classical computers can’t compute true random numbers, but real random numbers are critical for classical cryptography. Also Quantum cryptography has promising upsides with technologies likes Quantum Key Distribution (QKD). Not to be confused with QDK (Microsoft’ Quantum Development Kit), QKD leverages a quantum channel to send a symmetric / shared key between two parties which is then used to encrypt and decrypt data being sent over a classical channel. The quantum channel makes a man-in-the-middle attack physically impossible due to the Quantum mechanical principle that the Qubits state will collapse once it is accessed. So, if the attacker is eavesdropping the key, the receiver will know the Quantum state had changed before it was received at the end.
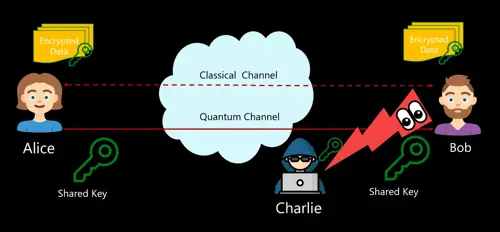
QKD networks require a fiber optic line between the parties but without any repeaters in-between since this would change the state. This of course limits the length of the network. However, in addition to the experimental deployments in the academic sector, there are already commercial usage of high-security networks evolving with hundreds of miles between the participants. QKD networks are also being tested for wireless transmission, where basically entangled photons are sent through the air. Fiber optics is a transmission medium for wired and the atmosphere for wireless, both cause scattering that also results in the entangled state change. Therefore, experiments are being conducted by various space agencies where the cryptography keys are sent as entangled photons from a satellite orbiting earth with results in much less atmospheric scattering.
QuBites Season 3 – Dancing with Quantum Security
Quantum Security is also a reoccurring topic for QuBites and with the brand-new season 3, we have quite a bit of new Quantum Security content coming soon. QuBites is a video series where we break down Quantum Computing concepts and use cases in short and easy to consume segments to help business leaders navigate and approach the complexity of quantum optimized computing. In each episode, we invite experts to discuss varying Quantum Computing topics and how businesses have already begun integrating this emerging tech to drive business outcomes today. Season 3 just kicked-off with a great episode where we interviewed Xenia Bogomolec, a multi-talented professional contemporary dancer and mathematician who now focuses on cryptography and other math-heavy cybersecurity topics, including Quantum Security.
Where to get started?
Valorem and the global Reply network are here to help with our experienced teams of security and Quantum Computing experts that can meet you where you are on your security journey and provide real ROI with Quantum Computing. If you have a security project in mind or would like to talk about your path to quantum-ready security, we would love to hear about it! Reach out to us as marketing@valorem.com to schedule time with one of our experts.
Also keep an eye on our social media pages and blog for future updates on Quantum Computing, and the brand new season 3 episodes of our QuBites video series, where we will cover related topics in short, bite-sized pieces with our panel of expert guests.








